Introducing Workflow Security Pack
Have you already started serious development with WF 4 and found security limitations?
Have you struggled to implement authenticated messaging, claims-based security, role-based security and other security features in workflow solutions?
WF 4 is a highly extensible framework so most of these features can be built using the WF extensibility model, but wouldn’t it be nice to have all of these security features available in an easy to use activity library?
Here comes the Workflow Security Pack (WFSP) project... WFSP is a collection of activities and associated plumbing to enable key security scenarios in WF 4. WFSP activities blend with the rest of the WF to bring end-to-end integrated security into workflow solutions. The following diagram shows the initial set of activities which are part of WFSP.
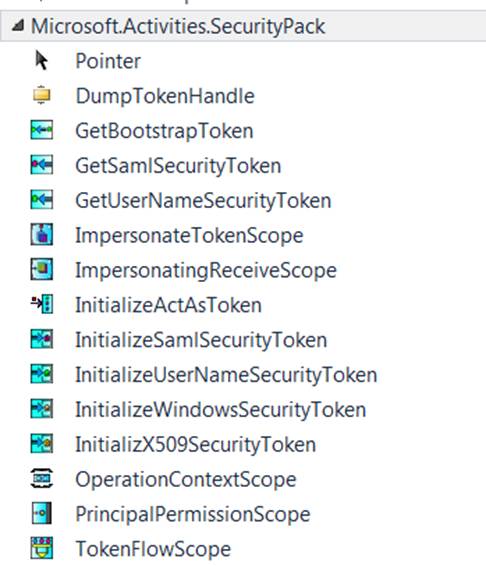
Following are some of the scenarios enabled by WFSP:
1. Authenticated messaging
a. Enables the use of various credentials with Send activity
b. Follows exactly the same model when using a Username token or a Saml token issued by an STS
2. Role-based security
a. Enables principal permission based authorization on the Receive activity
b. Supports standard RoleProvider extensibility model
3. Claims-based security
a. Ability to acquire a SAML token using the WS-Trust protocol
b. Ability to pass this token to a SAML secured service using WS-Security
4. End-to-end Claim-based delegation
a. Ability to use any token as an ActAs token
5. Transparent handling of tokens in a long-running environment
a. Enlisted tokens are preserved during persist and reload cycles
6. Impersonation and Delegation support
a. Ability to impersonate incoming Identity on Receive side
b. Ability to impersonate a User identity on the Send side
c. Ability to call a backend service from the Impersonated scope (Kerberos delegation)
7. WCF OperationContext access in a thread-agnostic way
In future posts, I’ll take an in-depth look into each of activities above and various scenarios enabled by these activities. Stay tuned.